Find True Search Query in Logs with Splunk
Find True Search Query in Logs with Splunk
Sometimes, each user typed characters in search query will be logged in logs, and it will cause the log to be like this:
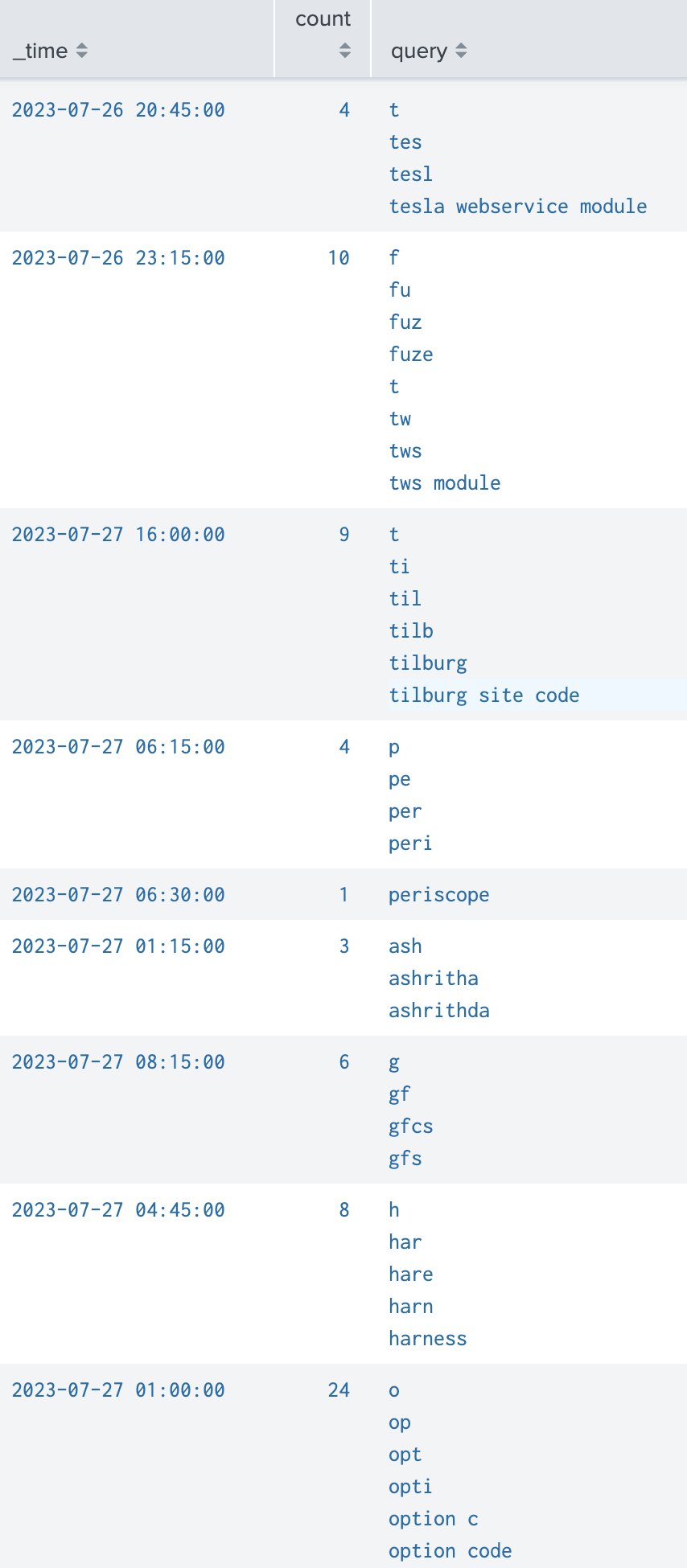
It will be difficult if we want to do some analysis or summary on these “overlapped” search queries.
Here is a way to only keep the true search query we want like following:
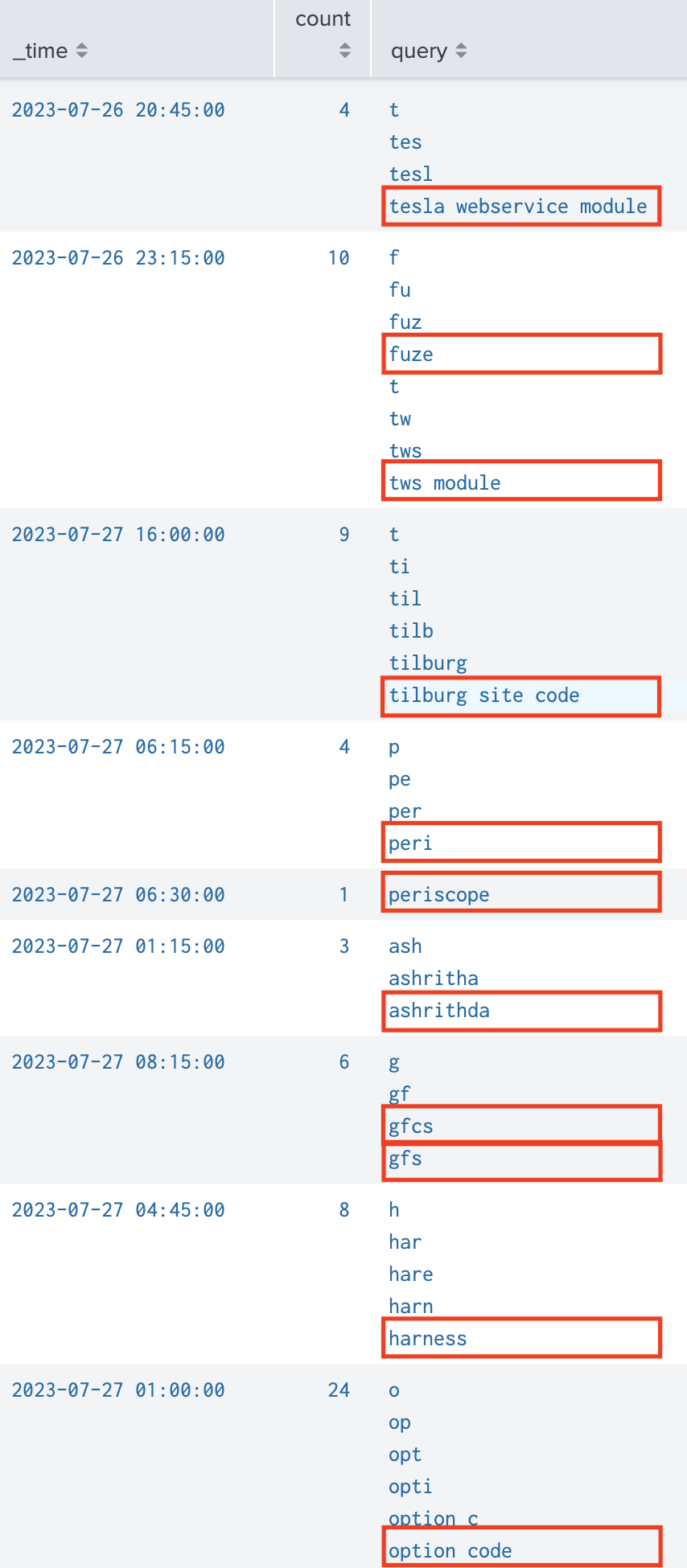
Out-Of-Box filtering
| `ut_shannon(query)` |
ut_shannon removes single letters, ut_meaning_ratio removes word and digit combination that doesn’t mean much, ut_bayesian removes all string that looks like DGA which can be used for random ID that is specific.
Catch
| stats values(query) as query values(http_uri) as http_uri values(index) AS idx values(sourcetype) AS st min(_time) as event_time by user timespan |
- Group the log via timespan and user
- Sort the result with timespan
- Expand the result with query field
- Create a new field “last_query” which will be the future value for field query
- If future value of query field contain the current value, set the flag to 0
- If future value of query field did not contain the current value, set the flag to 1
- Only keep the result with flag 1
- Group the result again
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Jindom's Blog!